📘 Note
You must be an Aptible organization owner to enable SCIM for your organization.
Step 1: Create a SCIM Integration in Aptible
- Log in to Aptible: Sign in to your Aptible account with OrganizationOwner privileges.
- Navigate to Provisioning: Go to the ‘Settings’ section in your Aptible dashboard and select Provisioning
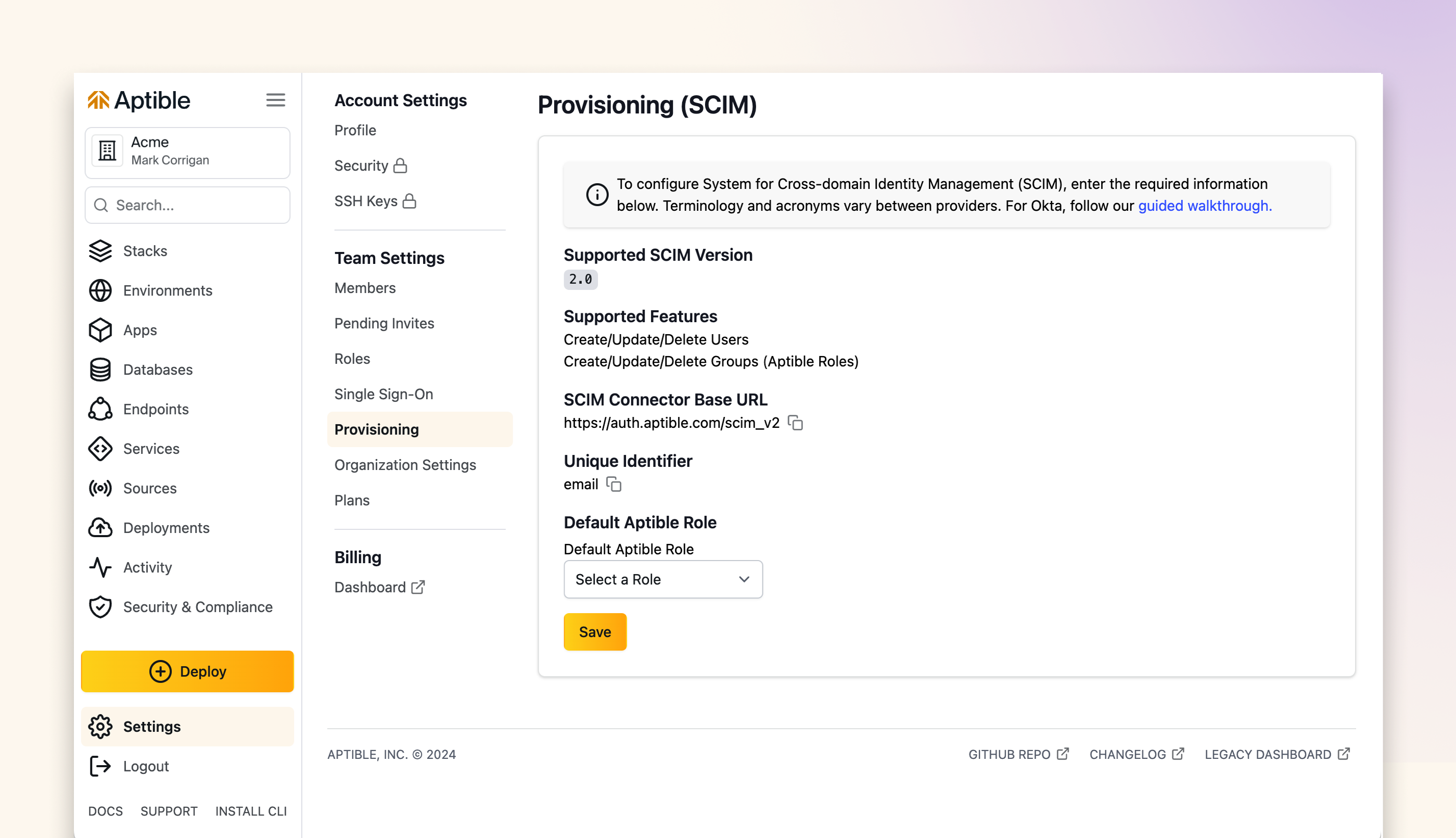
- Define Default Role: Update the Default Aptible Role. New Users created by SCIM will be automatically assigned to this Role.
- Generate SCIM Token: Aptible will provide a SCIM token, which you will need for the Okta configuration. Save this token securely; it will only be displayed once.
📘 Note
Please note that the SCIM token has a validity of one year.
- Save the Changes: Save the configuration.
Step 2: Enable SCIM in Okta with the SCIM test app
The SCIM 2.0 test app (Header Auth) is available in the Okta Integration Network, allowing you to enable user provisioning directly through Okta. Prior to enabling SCIM in Okta, you must configure SSO for your Aptible account To set up provisioning with Okta, do the following:- Ensure you have the Aptible SCIM token generated in the previous step.
- Open your Okta admin console in a new tab.
- Go to Applications, and then select Applications.
- Select Browse App Catalog.
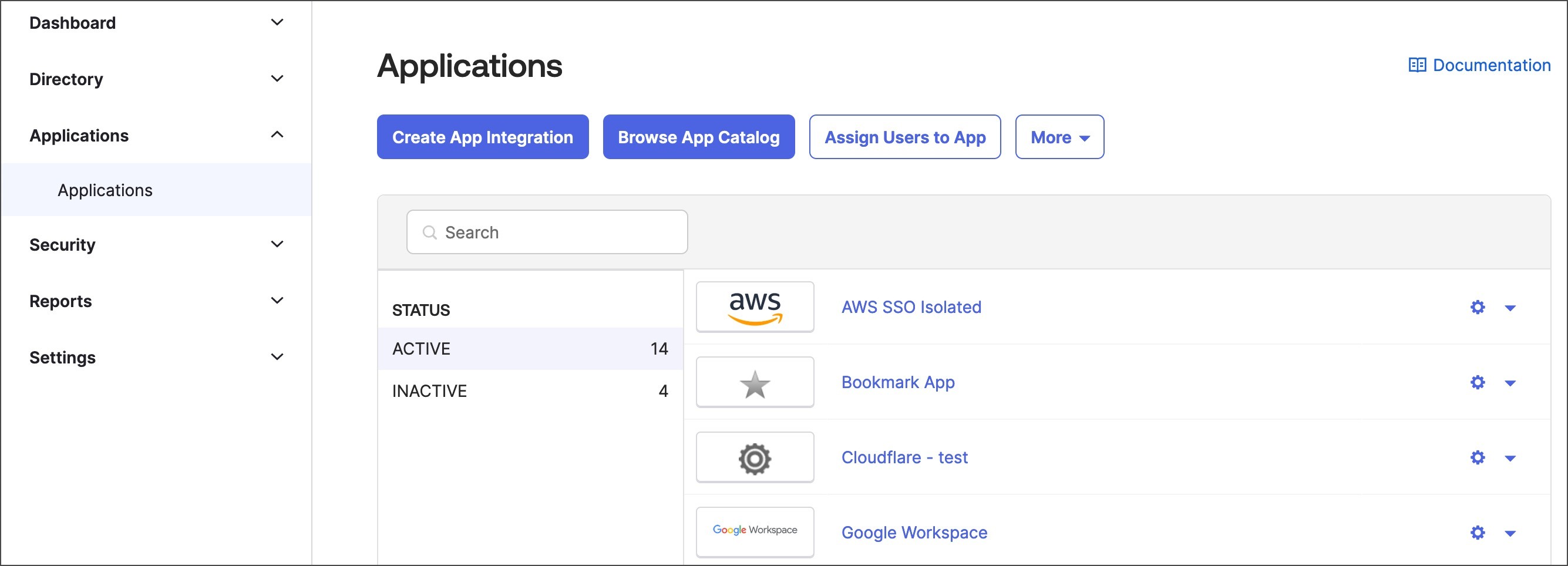
- Search for “SCIM 2.0 Test App (Header Auth)”. Select the app from the results, and then select Add Integration.
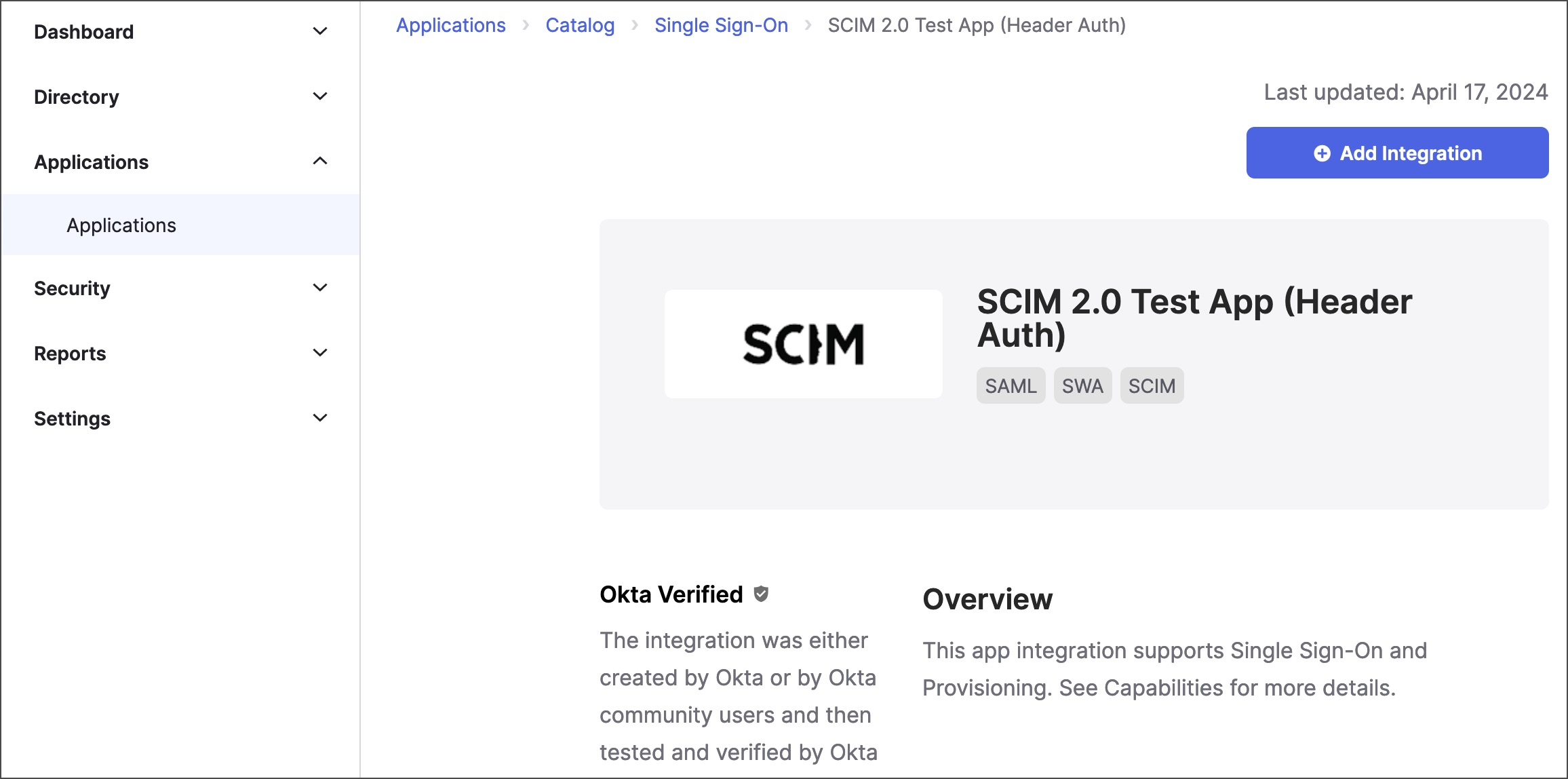
- In the General Settings tab, enter an app name you’ll recognize later, and then select Next.
- In the Sign-On Options tab, select Done.
- In Okta, go to the newly created app, select Provisioning, then select Configure API Integration.
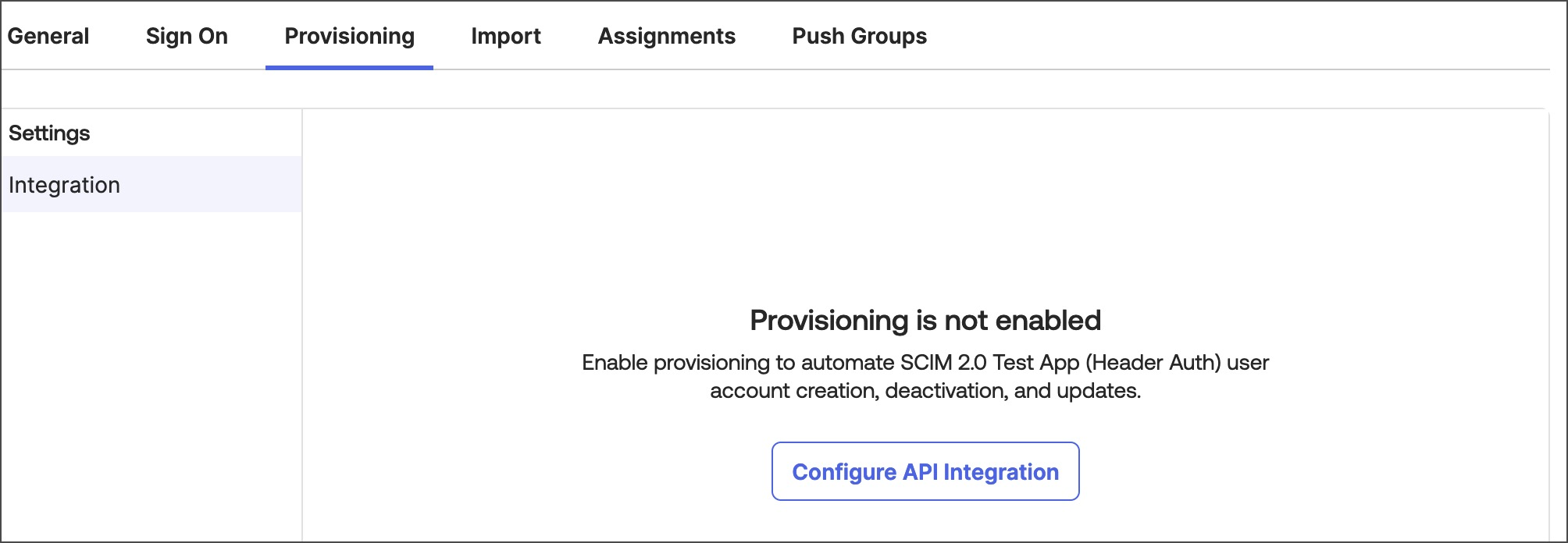
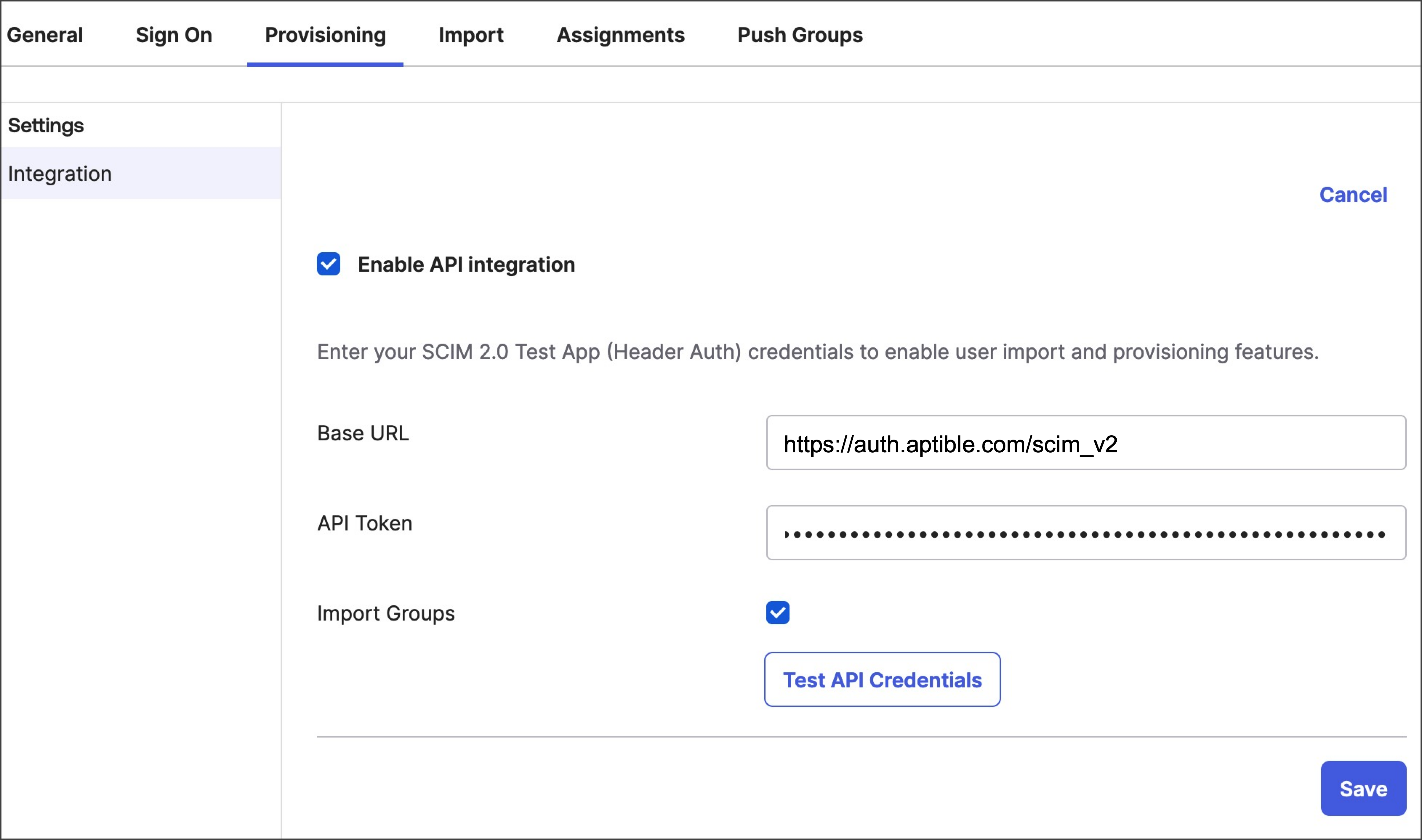
- Select Enable API integration, and enter the following:
- Base URL - Enter
https://auth.aptible.com/scim_v2. - API Token - Enter your SCIM API key.
- Base URL - Enter
-
Select Test API Credentials. If successful, a verification message will appear.
If verification is unsuccessful, confirm that you have SCIM enabled for your team in Aptible, are using the correct SCIM API key, and that your API key’s status is ACTIVE in your team authentication settings. If you continue to face issues, contact Aptible support for assistance.
- Select Save. Then you can configure the SCIM 2.0 test app (Header Auth).
Configure the SCIM test app
After you enable SCIM in Okta with the SCIM 2.0 test app (Header Auth), you can configure the app. The SCIM 2.0 test app (Header Auth) supports the provisioning features listed in the SCIM provisioning overview. The app also supports updating group information from Aptible to your IdP. To turn these features on or off, do the following:- Go to the SCIM 2.0 test app (Header Auth) in Okta, select Provisioning, select To App on the left, then select Edit.
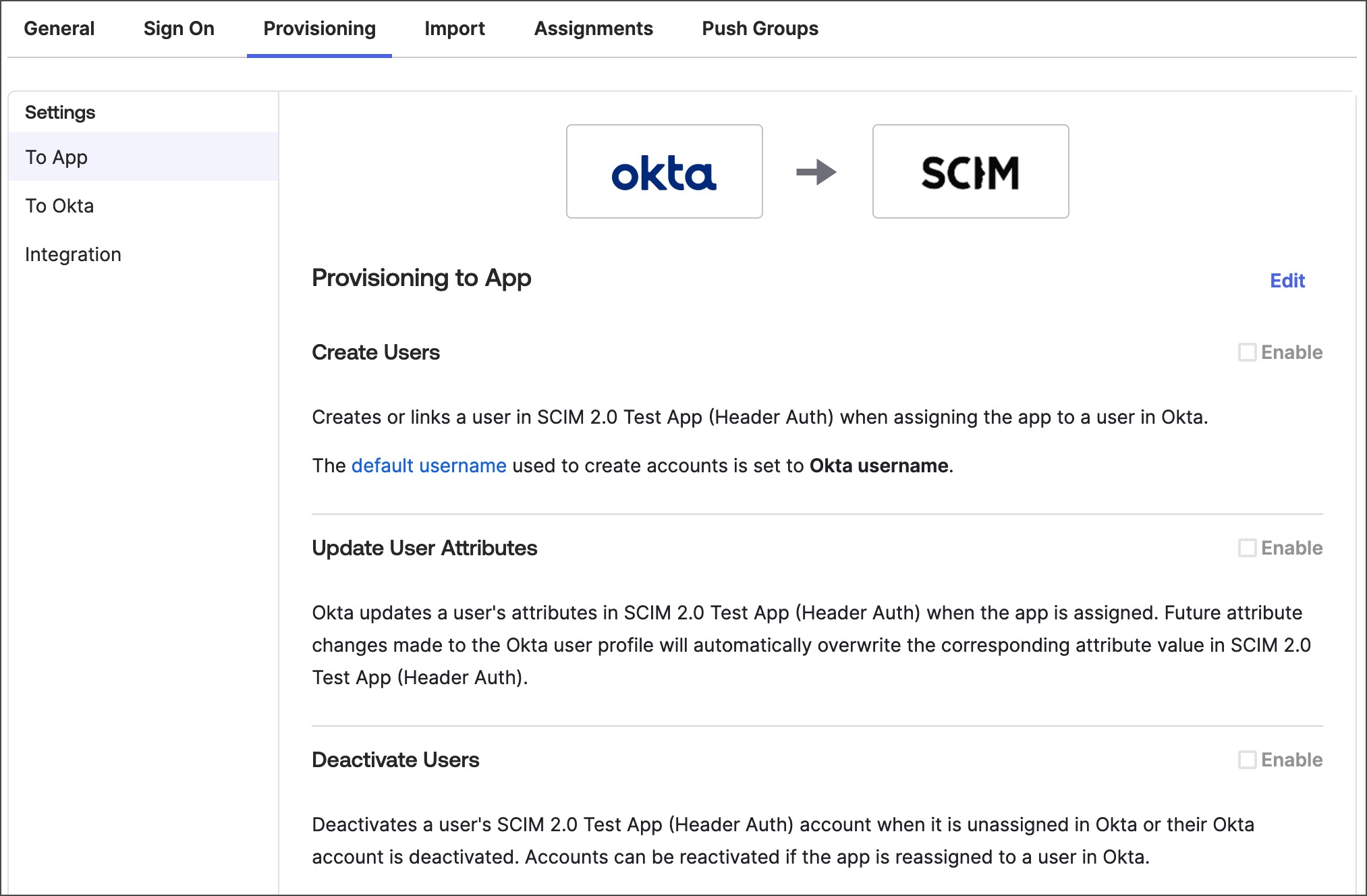
- Select features to enable them or clear them to turn them off. Aptible supports the Create users, Update User Attributes, and Deactivate Users features. It doesn’t support the Sync Password feature.
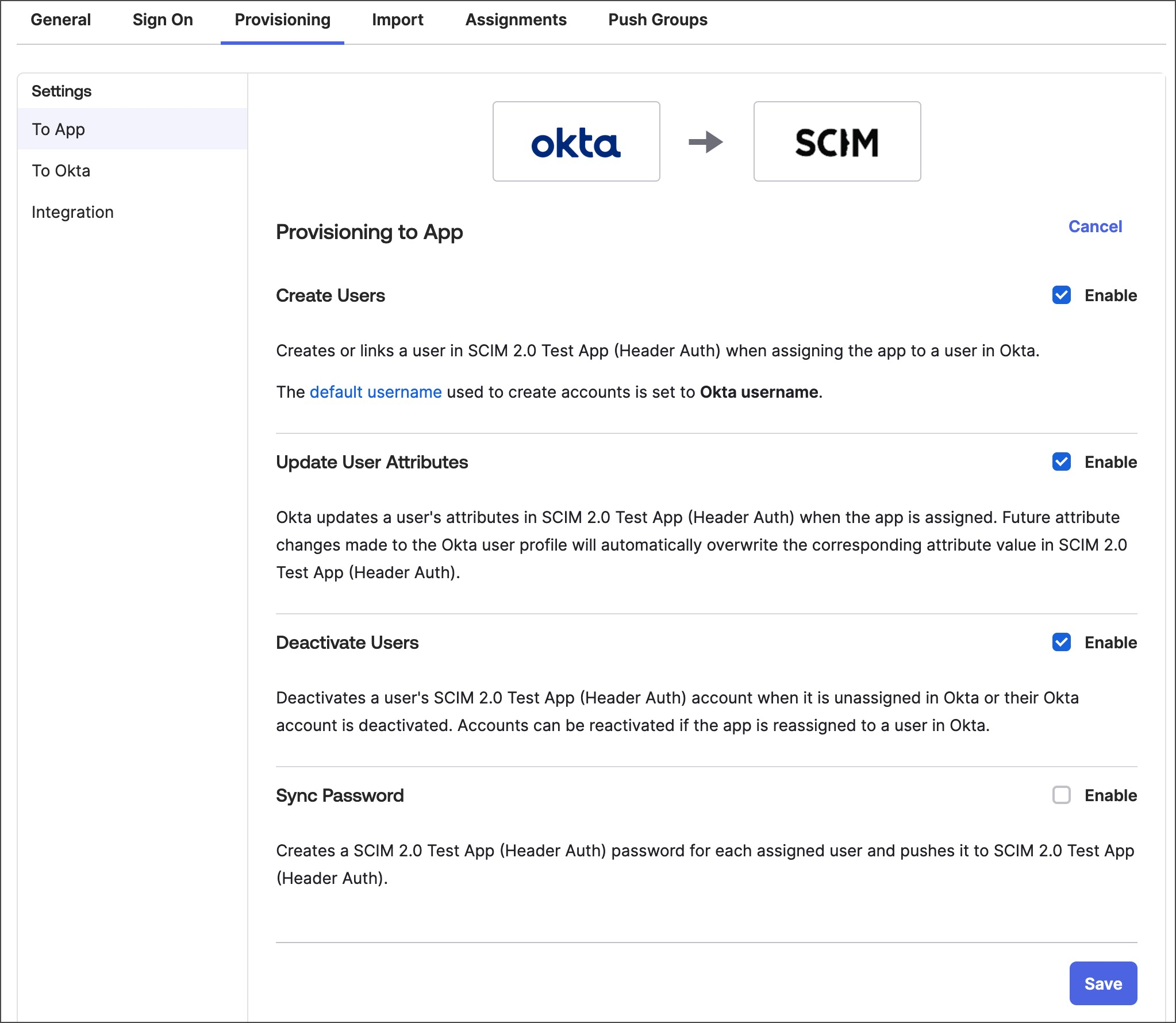
- Select Save to save your changes.
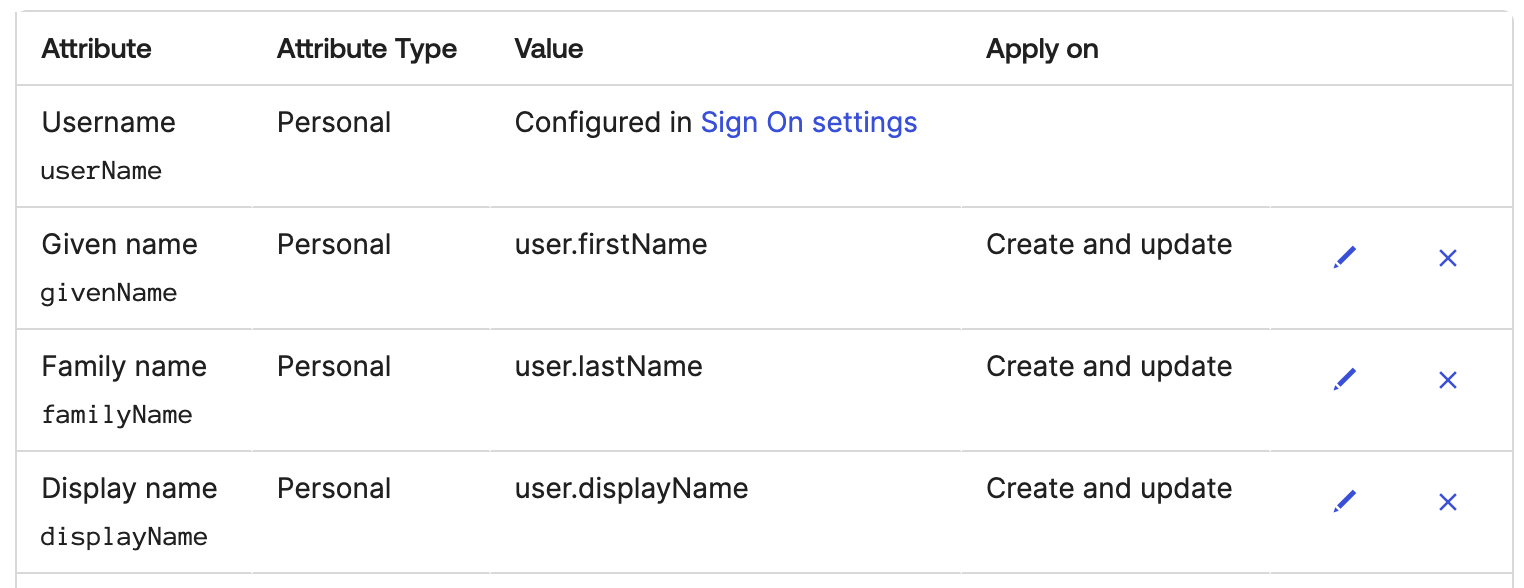
- Make sure only the Username, Given name, Family name, and Display Name attributes are mapped. Display Name is used if provided. Otherwise, the system will fall back to givenName and familyName. Other attributes are ignored if they’re mapped.
- Select Assignments, then assign relevant people and groups to the app. Learn how to assign people and groups to an app in Okta.
Step 3: Validate the SCIM Integration
- Validate User Provisioning: Create a test user in Okta and verify that the user is provisioned in Aptible.
- Validate User De-provisioning: Deactivate the test user in Okta and verify that the user is de-provisioned in Aptible.

