 gRPC Endpoints can be created using the
gRPC Endpoints can be created using the aptible endpoints:grpc:create command.
Like TCP/TLS endpoints, gRPC endpoints do not support
Endpoint LogsTraffic
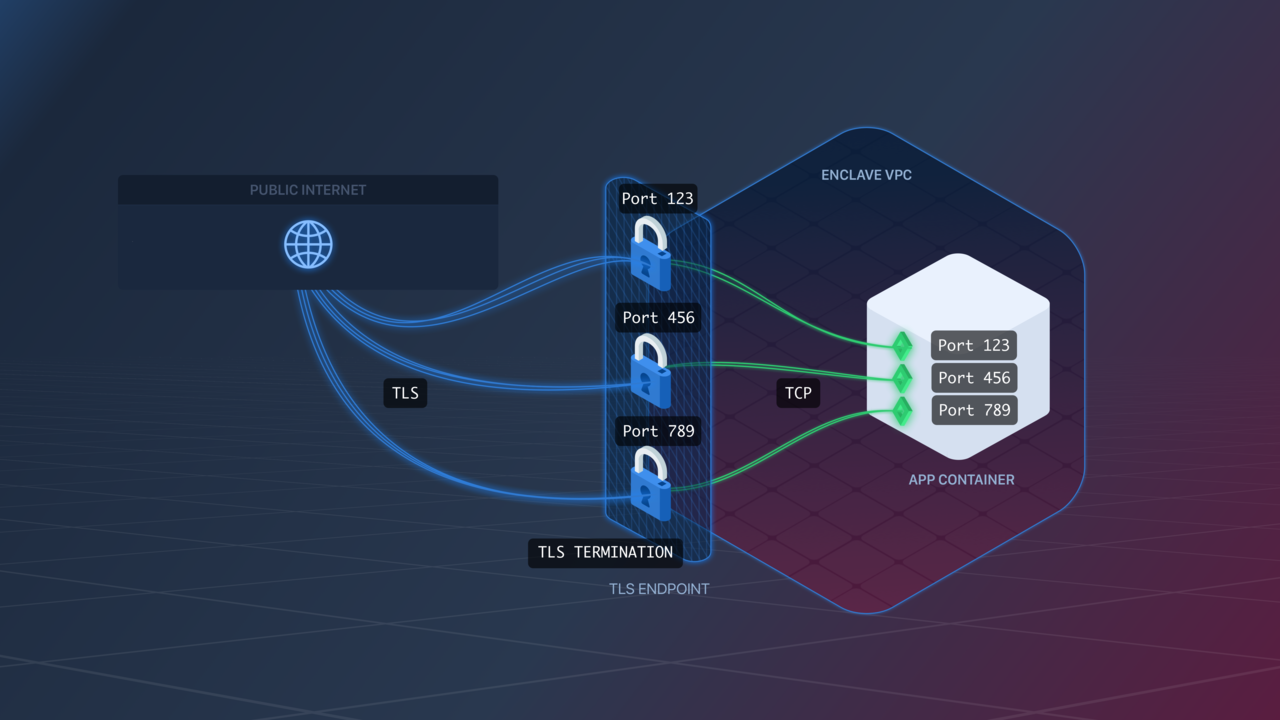
gRPC Endpoints terminate TLS traffic and transfer it as plain TCP to your app.
Container Ports
gRPC Endpoints are configured similarly to TLS Endpoints.
The Endpoint will listen for encrypted gRPC traffic on exposed ports and transfer it as plain gRPC traffic to your app over the same port. For example, if your Image exposes port 123, the Endpoint will listen for gRPC traffic on port 123, and forward it as plain gRPC traffic to your app Containers on port 123.
Zero-Downtime Deployment / Health Checks
gRPC endpoints provide Zero-Downtime Deployment by leveraging gRPC Health Checking.
Specifically, Aptible will use health/v1’s Health.Check call against your service, passing in an empty service name, and will only continue with the deploy if your application responds SERVING.
When implementing the health service, please ensure you register your service with a blank name, as this is what Aptible looks for.
SSL / TLS Settings
Aptible offer a few ways to configure the protocols used by your endpoints for TLS termination through a set of Configuration variables. These are the same variables as can be defined for HTTP(S) Endpoints. If set once on the application, they will apply to all gRPC, TLS, and HTTPS endpoints for that application.
SSL_PROTOCOLS_OVERRIDE: Control SSL / TLS Protocols
The SSL_PROTOCOLS_OVERRIDE variable lets you customize the SSL Protocols allowed on your Endpoint. The format is that of Nginx’s ssl_protocols directive. Pay very close attention to the format, as a bad variable will prevent the proxies from starting.
SSL_CIPHERS_OVERRIDE: Control ciphers
This variable lets you customize the SSL Ciphers used by your Endpoint.
The format is a string accepted by Nginx for its ssl_ciphers directive.
Pay very close attention to the required format, as here, again a bad variable will prevent the proxies from starting.
DISABLE_WEAK_CIPHER_SUITES: an opinionated policy
Setting this variable to true (it has to be the exact string true) causes your Endpoint to stop accepting traffic over the SSLv3 protocol or using the RC4 cipher.
We strongly recommend setting this variable to true on all Endpoints nowadays.
Examples
Set SSL_PROTOCOLS_OVERRIDE
aptible config:set --app "$APP_HANDLE" \
"SSL_PROTOCOLS_OVERRIDE=TLSv1.1 TLSv1.2"
Set DISABLE_WEAK_CIPHER_SUITES
# Note: the value to enable DISABLE_WEAK_CIPHER_SUITES is the string "true"
# Setting it to e.g. "1" won't work.
aptible config:set --app "$APP_HANDLE" \
DISABLE_WEAK_CIPHER_SUITES=true


